How to Report Product Security Vulnerabilities
If you discover any suspicious security vulnerabilities in any Shield eXtreme product, please report it to us. You can report potential cybersecurity vulnerabilities related to Shield eXtreme products to us by emailing ShieldX PSIRT(psirt@shieldx.io) and use ShieldX PSIRT PGP key to encrypt files.
When reporting product security vulnerabilities, please include the following information to help us speed up performing a risk assessment and provide remediation or mitigation measures:
- Product name and model
- Firmware/Software/Platform version
- Equipment and software needed to reproduce issues
- Steps to reproduce issues (attach pictures or codes if available)
- Proof-of-concept or exploit code to exploit the vulnerability
- Description of how attackers can take advantage of the vulnerabilities
- Capture the packets
- Any other information that you feel may be relevant
Updated:2022/O9/O1
Shield eXtreme is committed to ensuring cybersecurity of product , managing product potential risks in a rigorous manner, providing customers with reliable product quality, providing vulnerability mitigation guidelines and based on disclosed information, and minimizing the vulnerability-related risks.
Shield eXtreme has established the Product Security Incident Response Team (ShieldX PSIRT), responsible for handling incidents and related product vulnerability notifications reported to Shield eXtreme.
Shield eXtreme's commitment to cybersecurity of product is a priority, striving to maintain and improve the product's security level, continuously enhancing the security vulnerability handling process and response measures, and becoming a trusted partnership for customers.
Product Vulnerability Management Process
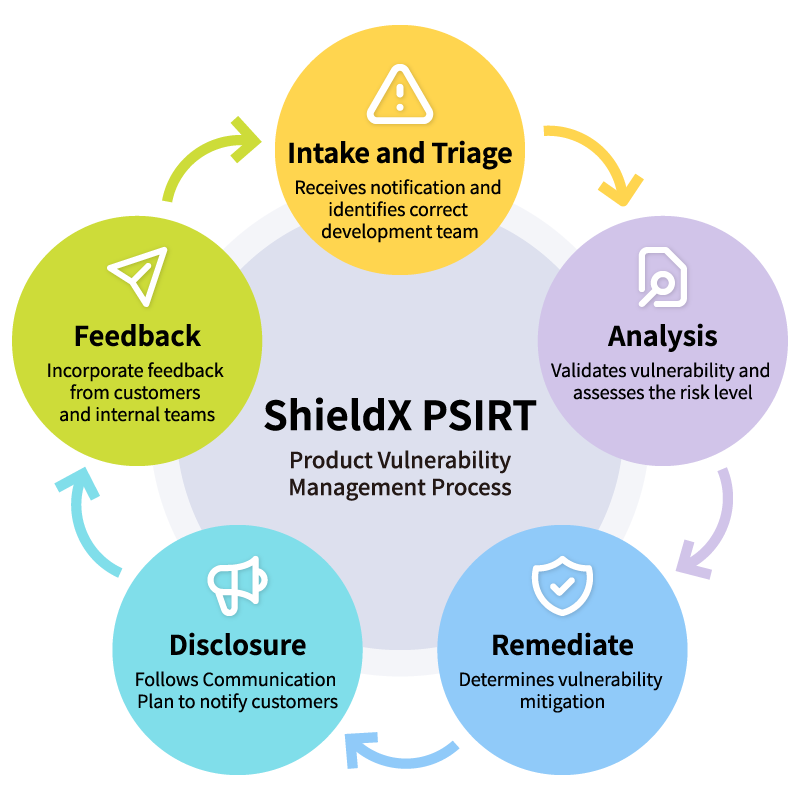
ShieldX PSIRT team evaluate the potential risk of a security vulnerability through the Common Vulnerability Scoring System (CVSS) based on the factors such as environment, likelihood of exploitation, and impact that could result from exploitation. This determines the timeline for addressing the vulnerability.
Upon confirming the potential impact on the Shield eXtreme product, Shield eXtreme sets up a dedicated test environment to further validate the effectiveness, severity, and impact of the vulnerability and communicates further with the reporter/security event notification organization as necessary. Once the root cause and impact of the vulnerability on the Shield eXtreme product have been determined, Shield eXtreme will perform repair analysis and provide a resolution or mitigation plan.
Updates and releases regarding product security announcements can be found on the "Product Security" page on the Shield eXtreme website. Besides the information provided in the security bulletin, version information, knowledge base articles, and frequently asked questions, Shield eXtreme does not provide specific information about vulnerabilities. Shield eXtreme does not distribute or release attack/proof-of-concept validation code for discovered vulnerabilities.
Disclaimer
Each section of the Cybersecurity Vulnerability Management Policy may be subject to change depending on each case. We do not guarantee the response to any specific issue. If you use the information contained in this document or the content linked to in this document, you do so at your own risk. Shield eXtreme reserves the right to modify any content in this policy at any time without prior notice. If there are any modifications, the revised document will be announced on the Shield eXtreme official website: www.shieldx.io.